A Critical Moment for Digital Preservation: The Internet Archive’s Struggle
Internet Archive's "The Wayback Machine" suffered a major data breach, after hackers gained access to the website and stole a user authentication database containing 31 million unique records.
News of the breach started to spread on Wednesday afternoon when visitors to the archive.org website saw a JavaScript alert, claiming that the internet archive was hacked.
About the Internet Archive
The Internet Archive is a nonprofit digital library founded in 1996, aiming to provide universal access to knowledge. It hosts a vast collection of books, websites, music, videos, and software. Its most notable tool, the "The Wayback Machine", allows users to view archived versions of websites. The Archive preserves cultural history by digitising and storing content, making it an essential resource for researchers, historians, and the public.Details of the Breach
"HIBP" refers to "Have I Been Pwned", a data breach notification service created by Troy Hunt, where hackers often share stolen data. Troy confirmed that the threat actor behind the Internet Archive breach shared the site's authentication database nine days ago. The stolen file, named "ia_users.sql," is a 6.4GB SQL file containing data like email addresses, screen names, Bcrypt-hashed passwords, and other internal information.
The most recent timestamp on the stolen records is from September 28th, 2024, which likely indicates when the database was taken. It contains 31 million unique email addresses, many of which are already subscribed to HIBP's service. This data has been added to HIBP, allowing users to check if their email was affected by the breach.
Verification and Disclosure
Troy Hunt verified the
authenticity of the breach by contacting users from the stolen database.
Among them was cybersecurity researcher "Scott Helme", who confirmed
that the "Bcrypt-hashed password" in the stolen data matched the one
stored in his password manager. Helme also verified that the timestamp
in the database matched the date when he last changed the password in his password manager.
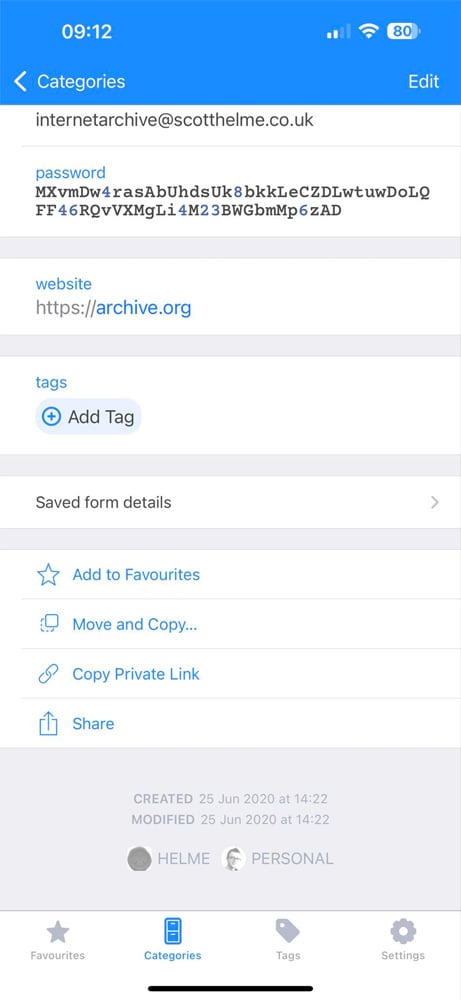
Source: Scott Helme
Internet Archive's Response
"Brewster Kahle", the founder of the Internet Archive, confirmed the data breach. Kahle shared an update stating that hackers used a compromised "JavaScript library" to display alerts on the site. He also mentioned that the site had faced "DDoS attacks" that were briefly fended off.
Kahle’s status update provided an overview of the situation:
- The website was defaced using a JavaScript library.
- Usernames, emails, and salted-encrypted passwords were stolen.
- The compromised JavaScript library was disabled, and the system is undergoing scrubbing and security upgrades.
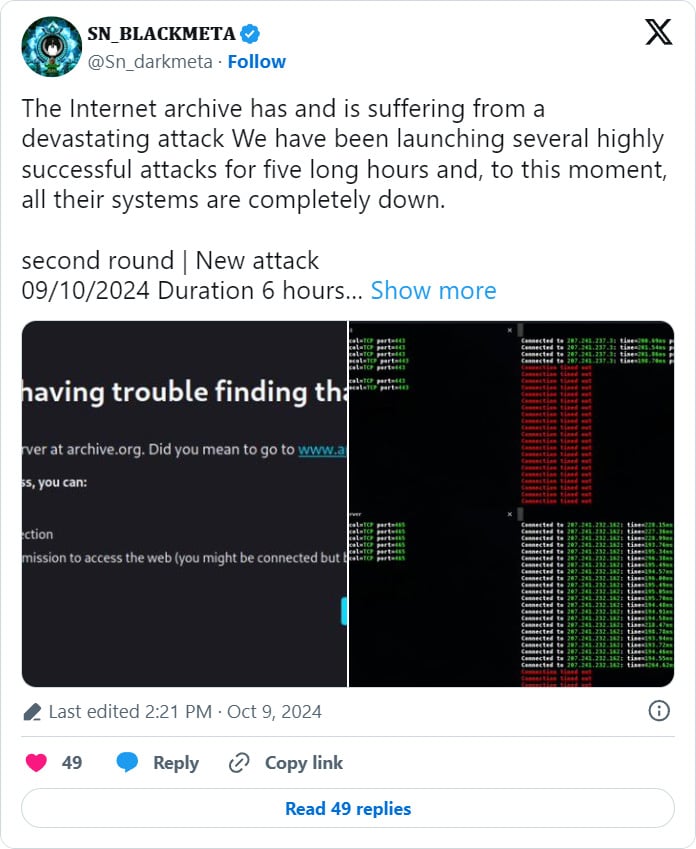
DDoS Attacks and Hacktivist Claims
Shortly
after addressing the data breach, the Internet Archive faced "renewed
DDoS attacks", taking both "archive.org" and "openlibrary.org" offline. The "BlackMeta hacktivist group" claimed responsibility for
these attacks, stating that more disruptions were planned.
Although
the Internet Archive is dealing with both a data breach and DDoS
attacks, it is not believed that the two incidents are connected.
Zendesk System Breach
In a further complication, the Internet Archive experienced
another breach yesterday, with hackers gaining access to their "Zendesk support
email system". The Archive is working to contain this new security
threat.
The Internet Archive breach highlights the growing threat to digital security and serves as a strong reminder to the importance of cybersecurity measures, even for trusted, longstanding institutions.
As data breaches become more frequent and increasingly sophisticated, organisations need to continuously review and enhance their security infrastructure to safeguard sensitive user information.
Users should take immediate steps like changing passwords and enabling multi-factor authentication to protect their data.
At Robust IT, we recommend organisations regularly update security protocols and train staff to prevent similar incidents. For professionals looking to strengthen their cybersecurity skills, our certifications, such as CompTIA Security+ and Certified Ethical Hacker, are essential for staying ahead and safe from emerging threats.



Comments
Post a Comment